The cybersecurity landscape is evolving faster than ever, and 2025 promises new challenges and opportunities. Here are the trends that will shape cybersecurity in 2025 and how you can prepare.
1. AI-Driven Cyberattacks
As artificial intelligence (AI) technology continues to evolve, so do the capabilities of cybercriminals leveraging it for malicious purposes. In 2025, AI-driven cyberattacks are expected to dominate the threat landscape. These attacks are faster, more sophisticated, and harder to detect than ever before.
Key Trends in AI-Driven Attacks
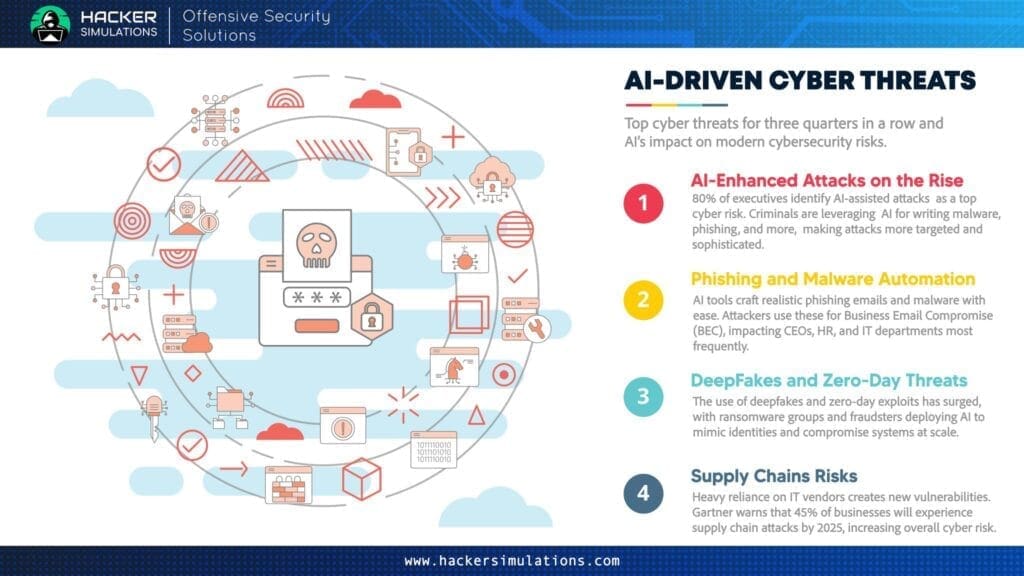
- AI-Enhanced Attacks on the Rise:(Ref) 80% of executives identify AI-assisted attacks as a top cyber risk. Criminals are leveraging AI for writing malware, phishing, and more, making attacks more targeted and sophisticated.
- Phishing and Malware Automation: AI tools craft realistic phishing emails and malware with ease. Attackers use these for Business Email Compromise (BEC), impacting CEOs, HR, and IT departments most frequently.
- Deepfakes and Zero-Day Threats: The use of deepfakes and zero-day exploits has surged, with ransomware groups and fraudsters deploying AI to mimic identities and compromise systems at scale.
- Supply Chain Risks: Heavy reliance on IT vendors creates new vulnerabilities. Gartner warns that 45% of businesses will experience supply chain attacks by 2025, increasing overall cyber risk.
Preparing for AI-driven threats now is essential to protect your organization’s data and reputation.
2. Remote Work Security Risks
The shift to remote and hybrid work has redefined the cybersecurity landscape. While it offers flexibility and scalability, it also introduces significant security risks that organizations must address in 2025.
Key Risks Facing Remote Work
- BYOD Policies: Personal devices often lack enterprise-grade security, making them easy targets for attackers.
- Unsecured Wi-Fi Networks: Remote workers frequently use public Wi-Fi, exposing sensitive data to interception.
- Human Error: Employees working remotely are more likely to fall prey to phishing attacks due to lack of direct IT oversight.
Recent Trends and Stats
- 22% of the American (Ref:) workforce will be remote by 2025 (Upwork Study).
- Around 20% of companies(Ref:) have experienced security breaches due to remote employees.
- BYOD-related incidents have surged, with 69% of remote workers (Ref) using personal devices for work tasks and 46% saving work files on personal devices.
- Co-working spaces have been identified as highly vulnerable.

By addressing these vulnerabilities, organizations can ensure secure and productive remote work environments in 2025.
3. Zero Trust Architecture
Data breaches are becoming increasingly sophisticated, prompting organizations to rethink traditional security approaches. Zero Trust Architecture (ZTA) has emerged as a leading strategy to combat these threats.
What Is Zero Trust?
Zero Trust is a security framework that assumes no user or device can be trusted by default, even if they are within the network perimeter. It operates on the principle of “never trust, always verify.”
Why Zero Trust Matters
- Growing Threat Landscape: With the rise of remote work and cloud adoption, traditional perimeter defenses are no longer sufficient.
- Regulatory Requirements: Compliance frameworks are increasingly incorporating Zero Trust principles.
Recent Trends and Stats
- 63% of organizations globally (Ref) have implemented a Zero Trust strategy, either fully or partially (Gartner Survey).
- The global Zero Trust security market is projected to reach $51.6 billion by 2028,(Ref) with a CAGR of 15.2%(Ref).
- 82% of cybersecurity professionals(Ref) are actively working on implementing Zero Trust, with 93% influenced by the White House’s announcement(Ref).

- Over 30% of organizations have a Zero Trust strategy in place, and 27% plan to implement it within six months. (Statista)
Key Components of ZTA
- Identity Verification: Continuous authentication of users and devices.
- Least Privilege Access: Users only access what they need for their role.
- Advanced Monitoring: Real-time analytics to detect anomalies.
Zero Trust is not a product but a journey, and organizations embracing it will be better equipped to handle the challenges of 2025.
4. Rising Compliance Requirements
With data breaches and privacy concerns at an all-time high, compliance with data protection regulations is more critical than ever. In 2025, organizations must stay ahead of evolving requirements or face significant penalties.
Key Regulatory Updates
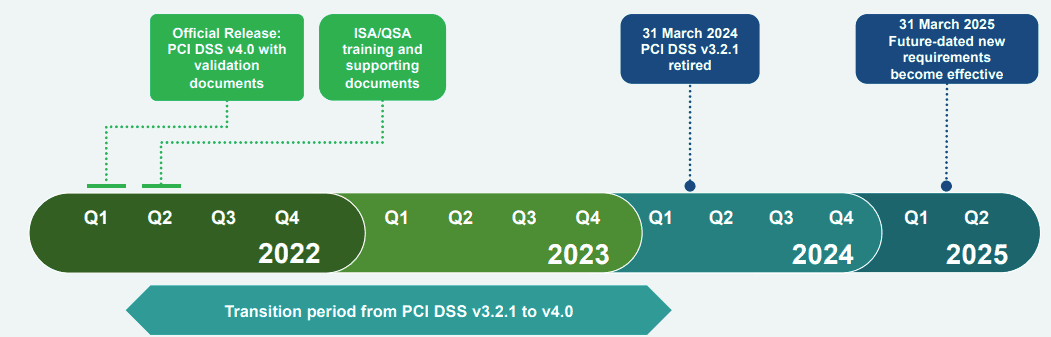
- PCI DSS: Major change: Transition to PCI DSS version 4.0, with new requirements for data protection and security controls.

- HIPAA: Focus areas include increased emphasis on patient privacy rights, robust cybersecurity practices, and stricter breach notification procedures. Staying updated on evolving interpretations and guidance from regulatory agencies is crucial.
- GDPR: While no major recent updates exist, ongoing enforcement actions and evolving case law remain important to monitor. Key aspects include ensuring proper data subject rights management and data minimization practices.
- ISO 27001: Transition to the ISO 27001:2022 standard with new and updated controls related to information security management. Deadline for updates: October 31, 2025.
- SOC 2: More rigorous reporting requirements to demonstrate robust security controls, including detailed documentation of data access controls and incident response capabilities.
- DORA Compliance 2025: Financial institutions in the EU or entities providing services to EU-based organizations must comply with the Digital Operational Resilience Act by January 17, 2025. Key aspects include:
- ICT Risk Management: Identify and mitigate IT system risks.
- Incident Reporting: Clear procedures for reporting cyber incidents.
- Resilience Testing: Regular tests, like penetration and scenario-based testing.
- Third-Party Risk Management: Address risks from vendors.
- Information Sharing: Collaborate on threat intelligence.
Organizations that prioritize compliance not only avoid penalties but also build trust with customers and stakeholders.
Let Us Help You
Preparing for the future starts today. Schedule a free consultation call with our experts to evaluate your business’s cybersecurity readiness. During the call, we’ll assess your current strategy, identify potential gaps, and recommend actionable steps to safeguard your organization in 2025 and beyond.