A 2019 Google study shows that 64% of people admit to reusing passwords across multiple sites which could create a “domino effect” that allows hackers to take down multiple accounts just by cracking one password.This is a problem because even if someone has a complex password, if they’re reusing it for many sites, a data breach at MySpace or Adobe could lead to the user’s account getting breached on your company’s site through a process known as credential stuffing.
The good news? There’s an easy way to better protect your accounts.
What is MFA?
Multi-Factor Authentication (MFA) is a critical aspect of modern security and a key factor in protecting sensitive information and assets. It adds an additional layer of security to traditional username and password authentication by requiring users to provide multiple forms of identification before accessing a system or application. Despite its importance, many organizations still lack this, leaving them vulnerable to cyber-attacks and data breaches. In this article, we will discuss why the lack of it is a security vulnerability and why organizations should implement this as part of their security strategy.
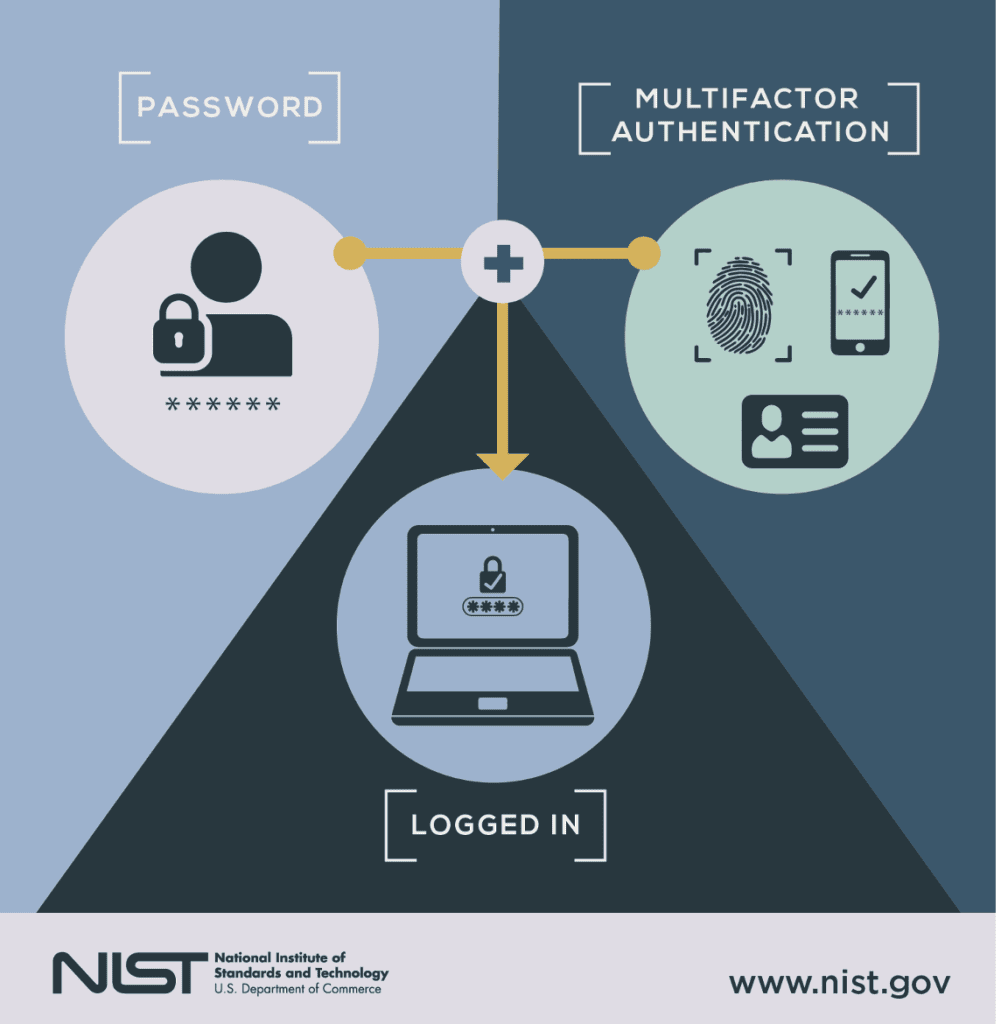
Credit: NIST/Natasha Hanacek
Why is MFA required for companies to have it implemented on their web applications?
MFA is a financial industry standard in which a user is required to provide additional verification when signing in according to Finra.
It helps protect you by adding an additional layer of security, making it harder for malicious actors to login as if they were you. Your information is safer because thieves would need to steal both your password and your phone.
A Google study showed that SMS based authentication “can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks”.
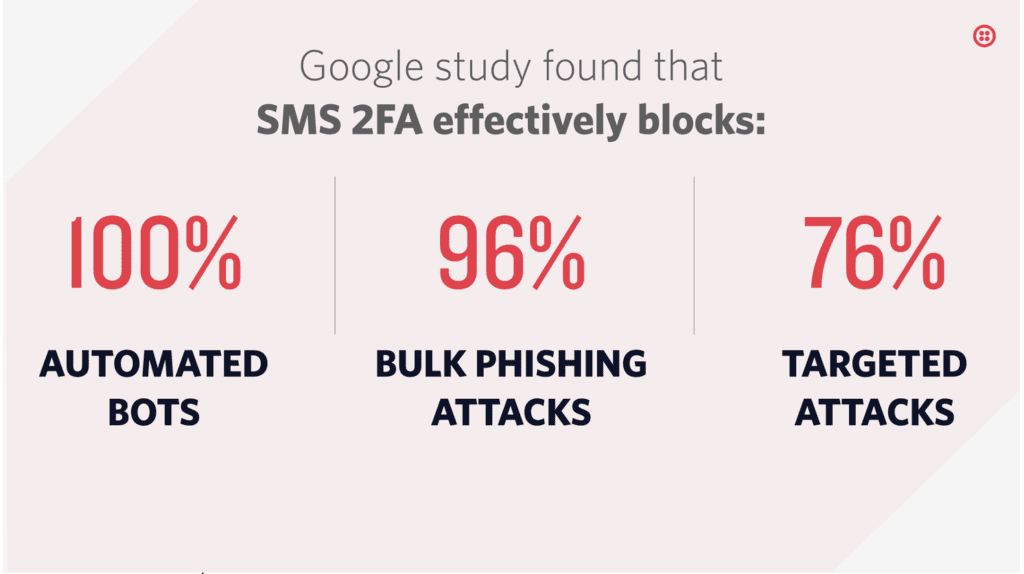
Source: twilio.com
How secure are your online accounts and how to improve their security?
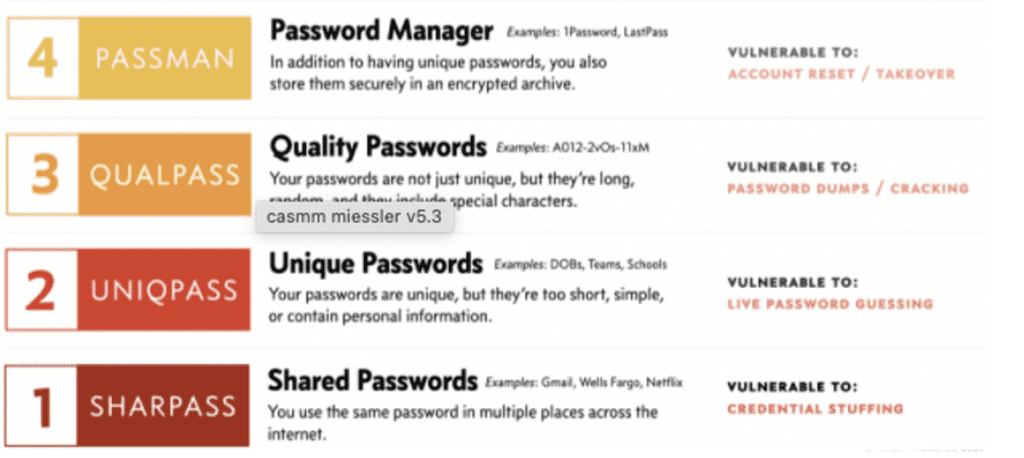
Using the following Consumer Authentication Strength Maturity Model (CASMM), created by Daniel Miessler, people with poor password hygiene can use it to improve their security rank.
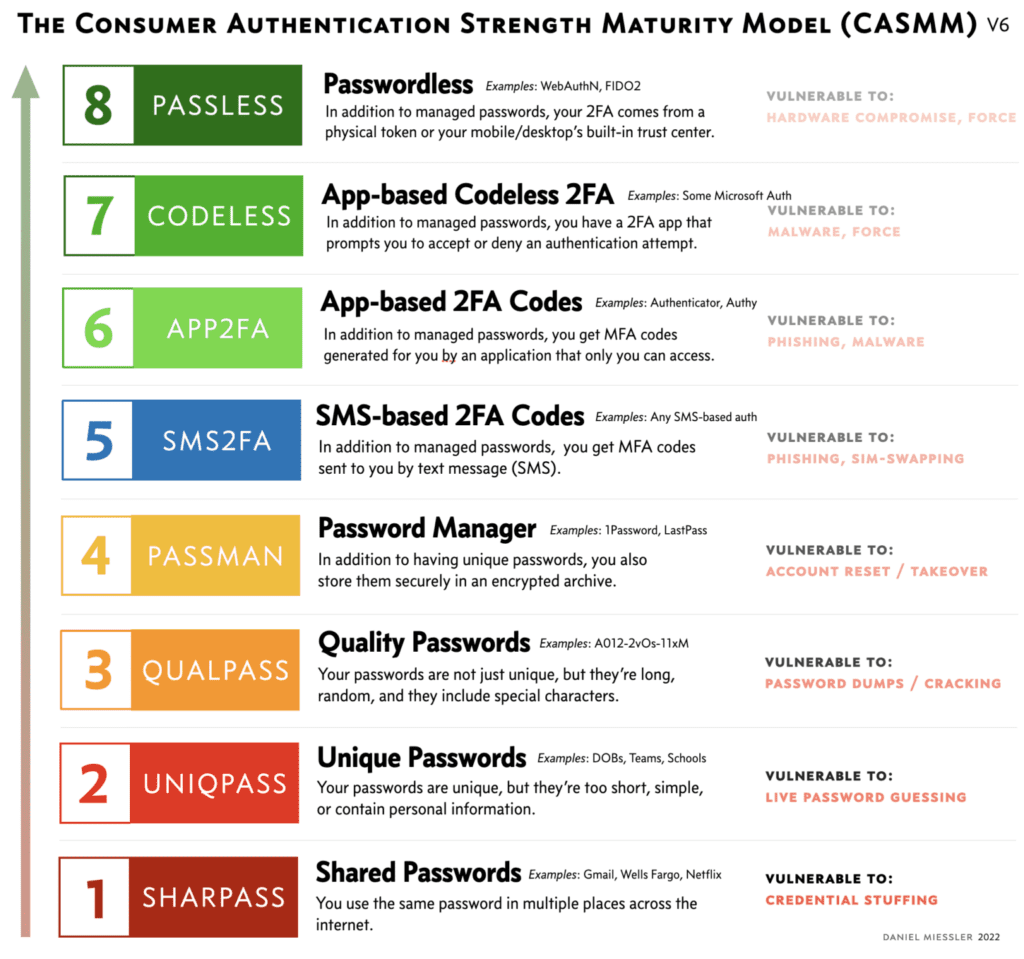
Source: The Consumer Authentication Strength Maturity Model (CASMM) v5 – Daniel Miessler.
Using this model, users can determine their level of security and improve accordingly to meet at least to Rank 5 (SMS-based 2FA)
NIST SP 800-63 REQUIREMENTS AND AUTHENTICATOR ASSURANCE LEVELS
The strength of an authentication transaction is characterized by an ordinal measurement known as the AAL. Stronger authentication (a higher AAL) requires malicious actors to have better capabilities and expend greater resources in order to successfully subvert the authentication process. Authentication at higher AALs can effectively reduce the risk of attacks.
It is required when any personal information is made available online. Since the other paths in this decision tree already drive the agency to an AAL that requires MFA, the question of personal information is only raised at this point. That said, personal information release at all AALs should be considered when performing the risk assessment. An important point at this step is that the collection of personal information, if not made available online, does not need to be validated or verified to require an AAL of 2 or higher. Release of even self-asserted personal information requires account protection via multi-factor authentication. Even though self-asserted information can be falsified, most users will provide accurate information to benefit from the digital service. As such, self-asserted data must be protected appropriately.
Authenticator Assurance Levels
Authenticator Assurance Level 1: AAL1 provides some assurance that the claimant controls an authenticator bound to the subscriber’s account. AAL1 requires either single-factor or multi-factor authentication using a wide range of available authentication technologies. Successful authentication requires that the claimant prove possession and control of the authenticator through a secure authentication protocol.
Authenticator Assurance Level 2: AAL2 provides high confidence that the claimant controls an authenticator(s) bound to the subscriber’s account. Proof of possession and control of two different authentication factors is required through secure authentication protocol(s). Approved cryptographic techniques are required at AAL2 and above.

Authenticator Assurance Level 3: AAL3 provides very high confidence that the claimant controls authenticator(s) bound to the subscriber’s account. Authentication at AAL3 is based on proof of possession of a key through a cryptographic protocol. AAL3 authentication requires a hardware-based authenticator and an authenticator that provides verifier impersonation resistance; the same device may fulfill both these requirements. To authenticate at AAL3, claimants are required to prove possession and control of two distinct authentication factors through secure authentication protocol(s). Approved cryptographic techniques are required.
Selecting AAL
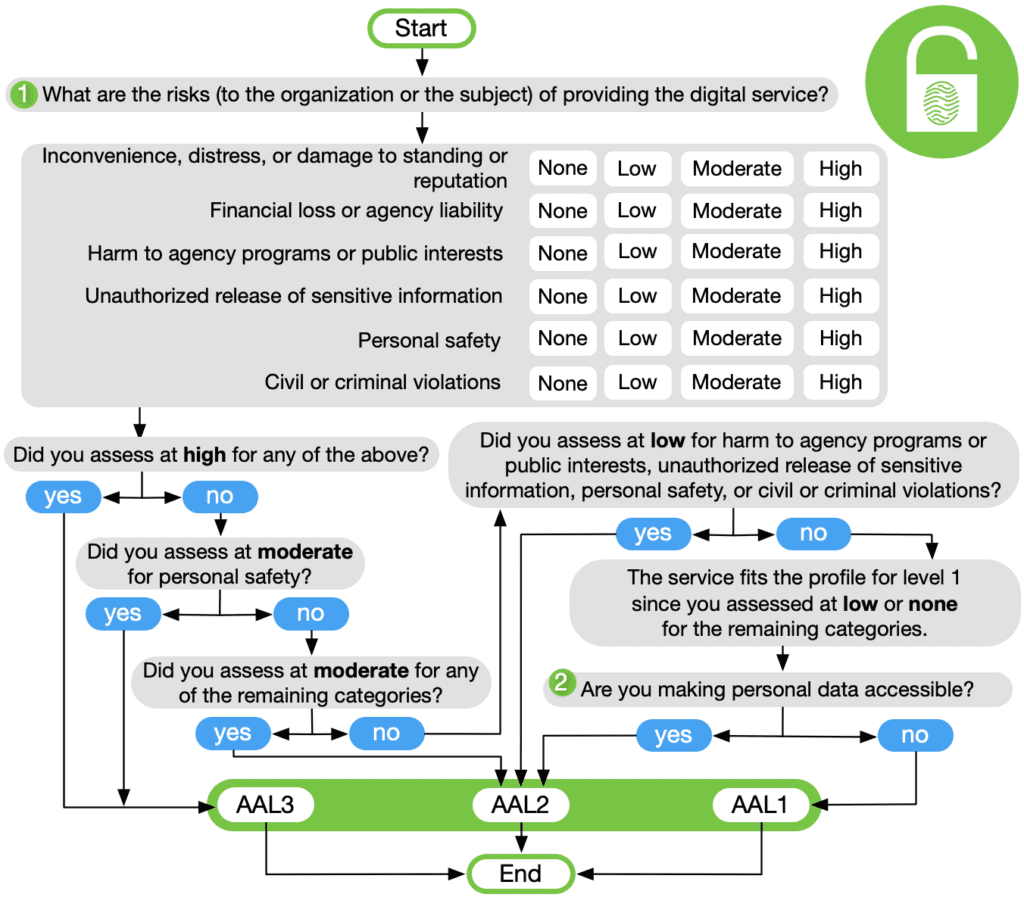
NIST SP 800-63-3: Selecting AAL Figure 6.2

NIST SP 800-63-3: Selecting AAL
CONCLUSION
Traditional username and password authentication has proven to be an inadequate form of security, with many organizations suffering data breaches due to weak or easily guessable passwords. In addition, many users reuse the same password across multiple systems and applications, making it easy for attackers to gain access to sensitive information.
This adds an additional layer of security to traditional username and password authentication by requiring users to provide additional forms of identification, such as a one-time code sent to their phone or a fingerprint scan. This makes it much more difficult for attackers to access sensitive information, as they would need access to multiple forms of identification.
In conclusion, the lack of multi-factor authentication is a security vulnerability that leaves organizations at risk of cyber-attacks and data breaches. It adds an additional layer of security to traditional username and password authentication and helps organizations protect sensitive information and assets. Organizations should implement this technology as part of their security strategy and educate their users on the importance of it in protecting sensitive information. By taking these steps, organizations can help ensure the security and privacy of their data and assets and maintain the trust of their customers and clients.
REFERENCES
https://www.finra.org/sites/default/files/2020-01/2020_CC_MFA.pdf
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63-3.pdf
https://pages.nist.gov/800-63-3/sp800-63-3.html
https://www.twilio.com/docs/glossary/what-is-two-factor-authentication-2fa
https://danielmiessler.com/blog/casmm-consumer-authentication-security-maturity-model/
https://pages.nist.gov/800-63-3/sp800-63b.html#sec4
https://www.nist.gov/back-basics-multi-factor-authentication
https://www.telesign.com/resource/telesign-consumer-account-security-report
https://security.googleblog.com/2015/07/new-research-comparing-how-security.html
https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html

