The benefits of Penetration Testing for SaaS Applications
In today’s rapidly evolving digital landscape, Software as a Service (SaaS) has experienced exponential growth, fueled by the need for flexible business solutions and by the COVID-19 pandemic, which precipitated a paradigm shift in work models, pushing organizations worldwide to embrace remote work and digital collaboration tools.
North America currently dominates the SaaS market share by 60%, catering to the evolving needs of both companies and customers alike. The global SaaS market is poised for exceptional growth, projected to expand by a staggering 349% to reach $1.23 trillion by the end of the decade (2032).
However, alongside the benefits of SaaS companies face challenges, and cybersecurity is one of the major ones. To fortify defenses and safeguard sensitive data, organizations are increasingly turning to penetration testing as a proactive security measure.
Security Challenges in SaaS Applications
SaaS applications, accessed via the internet and hosted on remote servers, are vulnerable to a myriad of cyber threats. Some of the common vulnerabilities include OWASP TOP 10 2021 for Web Applications and APIs:

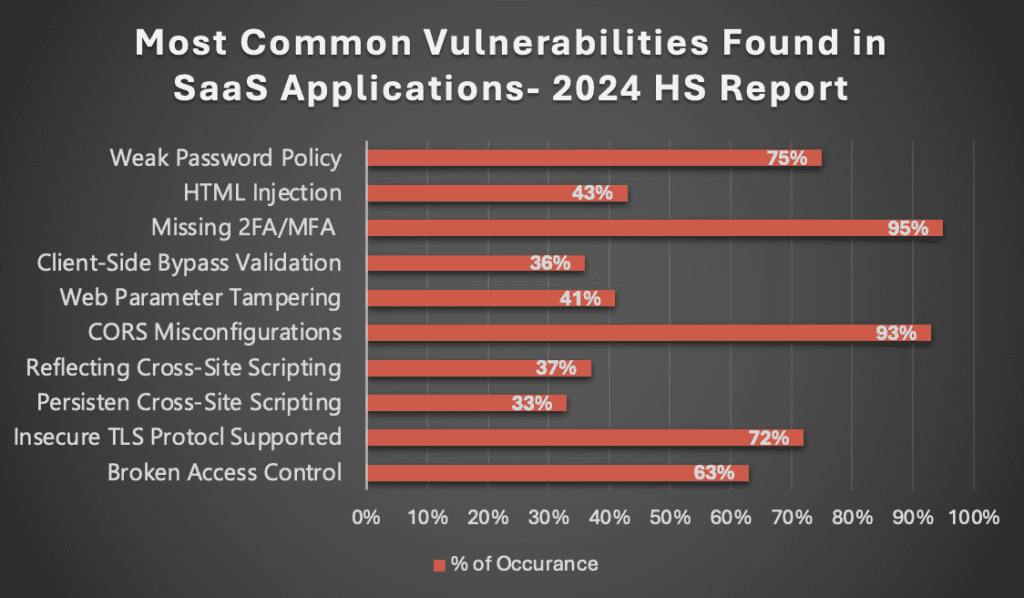
In recent penetration testing efforts on SaaS applications, Hacker Simulations has identified and categorized the most common vulnerabilities. As illustrated in the graph below, SQL injection and XSS were among the most frequently detected vulnerabilities, highlighting the critical need for robust security measures in SaaS development.
The repercussions of a security breach can be severe, ranging from financial losses and reputational damage to regulatory fines and legal consequences, like the recent SnowFlake Data Breach which impacted major companies like Ticketmaster, Santander Bank, AT&T, Advance Auto Parts, LendingTree, and QuoteWizard.
HOW TO SECURE SAAS APPLICATIONS ?
PERFORM REGULAR PENETRATION TESTS
Penetration testing (pen testing) is a crucial proactive measure to identify and address vulnerabilities before they can be exploited by malicious actors. Regularly scheduled pen tests help assess the security posture of your SaaS application and infrastructure. Key benefits include:
- Vulnerability Identification: Detecting and prioritizing vulnerabilities such as SQL injection, cross-site scripting (XSS), insecure APIs, and authentication weaknesses.
- Enhanced Security Measures: Implementing remediation strategies based on pen test findings to strengthen defenses.
- Compliance Requirements: Demonstrating adherence to regulatory and compliance standards by conducting periodic security assessments.
IMPLEMENT SAAS SECURITY CHECKLIST

A comprehensive SaaS security checklist ensures that fundamental security practices are in place throughout the development and deployment lifecycle of your application.
Download Our SaaS Security Checklist Questionnaire
ACHIEVE COMPLIANCE WITH INDUSTRY STANDARDS
Adhere to industry-specific compliance regulations and international standards:
- Data Protection and Privacy Regulations: GDPR, HIPAA, CCPA
- Financial Regulations: PCI DSS, SOX
- Industry-Specific Regulations: FERPA, GLBA, SOC 2
- International Standards: ISO/IEC 27001
- Miscellaneous Regulations: COPPA
INCLUDE PENETRATION TESTING IN SDLC CYCLE
Integrating penetration testing into the SDLC ensures that security is a continuous and integral part of software development and deployment:
- Planning: Define pen testing scope and objectives based on project requirements and risk assessment.
- Development: Conduct static and dynamic testing to identify vulnerabilities in code and application architecture.
- Testing: Perform comprehensive pen tests to validate security controls and configurations.
- Deployment: Verify security posture post-deployment to mitigate risks before production release.
Best Practices for Effective SaaS Penetration Testing?
Why Should SaaS Startups Perform Penetration Testing?
For SaaS startups, security is a cornerstone of customer trust and brand reputation. Penetration testing helps identify vulnerabilities before they can be exploited by malicious actors, ensuring that your platform is secure from the outset. As your customer base grows, so does the potential attack surface, making it crucial to regularly test your defenses. Early and consistent penetration testing not only helps prevent breaches but also demonstrates to investors, customers, and partners that you take security seriously.
Common Types of Penetration Testing for SaaS
For SaaS platforms, the most common types of penetration testing include:
- Web Application Testing: This is essential for identifying vulnerabilities in the core application that could be exploited by attackers.
- API Testing: Since SaaS applications often rely heavily on APIs, testing these interfaces is critical to ensure they are secure against unauthorized access and data breaches.
- Cloud Security Testing: Given that SaaS solutions are typically hosted in the cloud, evaluating the security of cloud environments, including configurations, is a vital part of the testing process.
- Internal Network Penetration Testing: For SaaS companies with an internal network, even in a remote or hybrid setup, testing internal network defenses can help identify potential vulnerabilities that could be exploited by insiders or during an external breach.
- Mobile App Penetration Testing: If your SaaS offering includes a mobile application, it’s crucial to test for vulnerabilities specific to mobile platforms, ensuring that both the app and the data it handles are secure.
How to Choose the Right Penetration Test Provider?
Selecting the right pentest provider is crucial for obtaining actionable insights. Look for a provider with:
- Industry Experience: Choose a team with specific experience in testing SaaS applications, including knowledge of cloud environments and modern development practices.
- Comprehensive Reporting: Ensure the provider offers detailed reports that not only highlight vulnerabilities but also provide clear remediation guidance.
- Customization Options: The best providers tailor their testing methodologies to your specific SaaS architecture and security needs, whether it’s a black box, white box, or gray box approach.
- Proven Track Record: Check references, case studies, or testimonials from other SaaS companies to verify the provider’s effectiveness and reliability.
By following these best practices, SaaS startups can bolster their security posture, protect customer data, and build a solid foundation for growth.

