Single Sign-On (SSO) platforms like Okta and Microsoft Entra ID (Azure AD) are foundational to modern enterprise security — and that’s exactly why attackers are targeting them. In early 2026, threat actors linked to ShinyHuntersclaimed responsibility for multiple SSO-related data theft campaigns, raising alarms across the cybersecurity community.
What Happened?
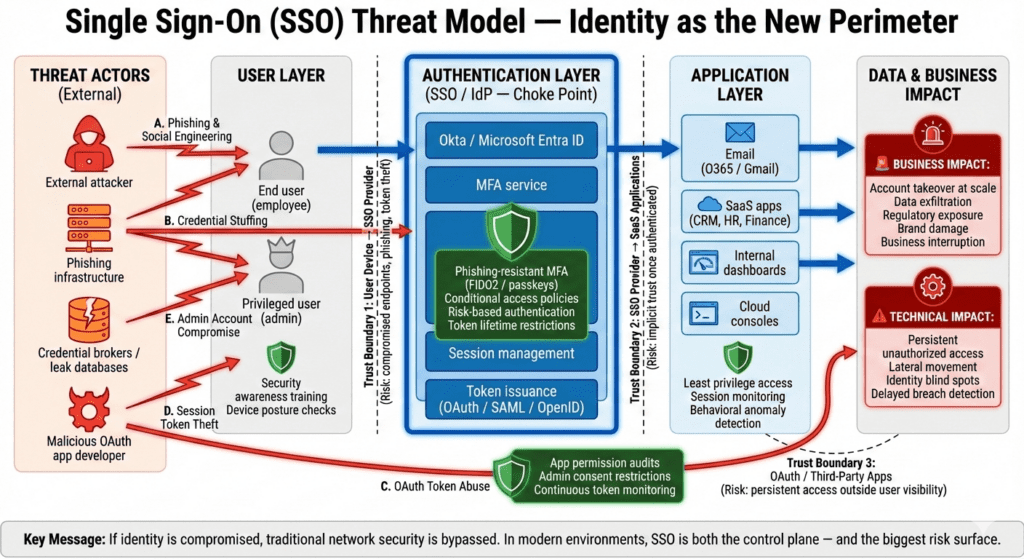
The attacks reportedly focused on stealing SSO account data, including credentials, session tokens, and identity metadata. Rather than exploiting a single vulnerability, attackers leveraged a combination of:
- Phishing campaigns targeting SSO users and admins
- Credential stuffing using previously leaked passwords
- OAuth token abuse and over-permissioned applications
- Weak or misconfigured MFA policies
This reinforces a growing trend: identity is now the primary attack surface.
Why SSO Is Such a High-Value Target
SSO systems sit at the center of cloud access. Compromising one account often means:
- Access to email, SaaS platforms, and internal dashboards
- Lateral movement across cloud and on-prem environments
- Persistent access via OAuth tokens that bypass passwords entirely
In many environments, breaching SSO is effectively breaching the company.
Key Attack Techniques Used Against SSO in 2026
1. OAuth Abuse
Attackers register malicious or compromised OAuth apps to gain persistent access without triggering login alerts.
2. MFA Bypass & Fatigue Attacks
Push fatigue and social engineering are still effective where phishing-resistant MFA is not enforced.
3. Session Token Theft
Stealing valid session cookies allows attackers to bypass authentication altogether.
4. Admin Account Targeting
SSO administrators are increasingly singled out, as one compromised admin account can expose thousands of users.
Security Gaps These Attacks Expose
- Over-trusted identity providers
- Excessive permissions granted to third-party apps
- Inconsistent MFA enforcement
- Limited visibility into identity telemetry
How Organizations Should Defend SSO in 2026
Technical Controls
- Enforce phishing-resistant MFA (FIDO2, passkeys)
- Audit OAuth applications and revoke unused tokens
- Enable conditional access policies and device trust
- Monitor for anomalous login and token behavior
Business & Governance Controls
- Treat identity systems as Tier 0 assets
- Limit admin privileges and apply just-in-time access
- Run regular identity threat modeling exercises
- Train users on modern phishing and MFA abuse techniques
Final Takeaway
SSO platforms like Okta and Microsoft aren’t “broken” but they are increasingly targeted. The lesson from these attacks is clear: securing identity is no longer optional or secondary. In 2026, identity security is cybersecurity.
This is where Hacker Simulations comes in.
We don’t train staff or run tabletop exercises we simulate real-world identity attacks against your SSO, MFA, session handling, and conditional access controls. Our penetration testing approach exposes exactly how identity systems fail under active adversary pressure before attackers do it for real.

