
Project Details
- Client : SAAS Payment Platform
- Date : 2021
- Category : Web Application Pentesting
- Location : California, USA
How Hacker Simulations helped a SAAS Company secure their customers data?
Our client, a prominent provider of Software as a Service (SaaS) payment solutions, approached us with the primary objective of conducting a comprehensive penetration test on their platform to ensure Payment Card Industry Data Security Standard (PCI DSS) compliance. The platform, designed for online payments, allowed users to store sensitive financial such as:
Account and Routing Numbers, Credit Card Numbers, Funds on the Account
and PII ( Personable Identifiable Information) on the platform such as:
First & Last Name, DOB, SSN, Home/Business Address, Email Address
- Objective: The client hired Hacker Simulations to conduct a security assessment to meet PCI DSS compliance requirements, which mandate regular security assessments to identify and rectify any vulnerabilities that could compromise the security and integrity of user data and the overall functionality of the payment platform.
- Methodology: Hacker Simulations used a combination of automated tools and manual techniques to identify vulnerabilities in the platform.
Discovery of IDOR Vulnerability
During the thorough examination of the system, our penetration testing team discovered a critical Insecure Direct Object Reference (IDOR) vulnerability. This vulnerability allowed unauthorized access to other customers’ accounts, posing a significant threat to the security of the platform and the confidential information stored within it.
Insecure Direct Object Reference (IDOR) vulnerability: Our Pen Testers found an IDOR vulnerability that could allow an attacker to take over a user’s account by changing the account ID parameter in the URL.

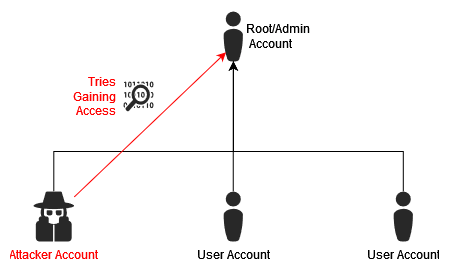
Exploitation and Potential Impact
Upon successful exploitation of the IDOR vulnerability, our team demonstrated the ability to take over other customers’ accounts. This could have given an attacker unauthorized access to sensitive financial information, enabling them to view and manipulate account and routing numbers, credit card details, and available funds. Additionally, access to PII, including names, dates of birth, social security numbers, addresses, and email addresses, could be misused for identity theft and fraudulent activities.
The potential impact of a malicious actor discovering and exploiting this vulnerability before mitigation could have been catastrophic. An attacker could have initiated unauthorized fund transfers to overseas bank accounts, causing financial losses to customers. Furthermore, the compromise of sensitive PII could lead to severe harm to the affected individuals, tarnishing the reputation of both the payment platform and our client.
Other High Vulnerabilities Found
- Priviledge Escalation
- Password Reset Token Bypass
- Cookie Manipulation
- Misconfigured API Endpoints
14
5
Mitigation Recommendations and Outcome
Hacker Simulations provided a detailed report to the client, outlining the vulnerabilities that were identified and the potential impact of these vulnerabilities.
We worked closely with our client to implement immediate and robust mitigation measures. These measures, crucial for maintaining PCI DSS compliance, included patches to address the vulnerabilities, enhanced access controls, and thorough testing to ensure the effectiveness of the fixes.
The client was able to use the report to address the vulnerabilities and improve the overall security of their platform. The discovery and successful remediation of the vulnerabilities underscore the critical role that penetration testing plays in ensuring the security and compliance of SaaS platforms. By addressing these vulnerabilities and implementing robust mitigation measures, our client not only protected the integrity of sensitive user data but also took significant strides towards achieving PCI DSS compliance.
They continue to work with our company to conduct regular security assessments to ensure ongoing protection against potential threats.

