
Project Details
- Client : Web Application
- Date : 2023
- Category : Web Application Pentesting
- Location : Miami, Florida, USA
How Hacker Simulations helped an AI Company secure their customers data?
Our client, a prominent provider of AI solutions provider, approached us with the primary objective of conducting a comprehensive penetration test on their platform to ensure SOC2 compliance.
Objective: The primary objective was to identify and address potential vulnerabilities, ensuring the protection of sensitive information and upholding the organization’s commitment to data security.
Methodology: Our penetration testing approach involved a combination of automated tools and advanced manual testing techniques developed by our threat intelligence team. The latter played a crucial role in identifying complex vulnerabilities that automated scans might overlook. By simulating real-world attack scenarios, we aimed to uncover vulnerabilities that could compromise the confidentiality, integrity, and availability of the web application.
Discovery of SQL Injection Vulnerability
During the manual testing phase, our pentesting team identified a critical SQL Injection (SQLi) vulnerability within the web application. This type of vulnerability allows malicious actors to manipulate the application’s database queries, potentially leading to unauthorized access and extraction of sensitive information.
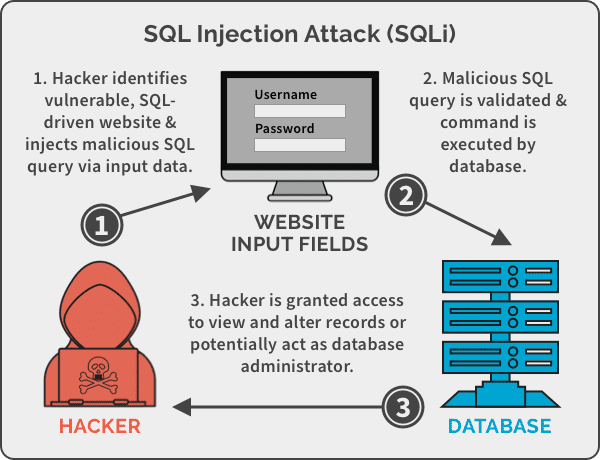
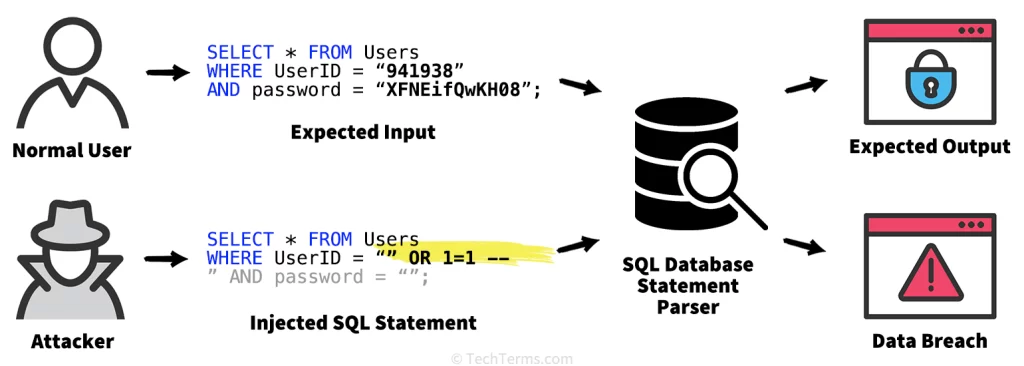
Exploitation and Potential Impact
Upon discovering the SQL Injection vulnerability, our team executed a controlled exploit to assess the extent of the risk. By carefully crafting SQL queries, we were able to retrieve a significant amount of sensitive information from the application’s database. The compromised data included:
Billing details, confidential employee records, internal financial data,
and sensitive client information (SSN, First and Last Name, Phone, Email, Home Addres).
The potential impact of the SQL Injection vulnerability could be profound. A malicious actor exploiting this vulnerability could gain unauthorized access to sensitive business and personal information, leading to financial losses, reputational damage, and regulatory non-compliance. The compromised data can pose a direct threat to the confidentiality of the organization’s operations, employee records, and client relationships.
Other High Vulnerabilities Found
- Reflected XSS
- Broken Access Control
- Reflected XSS
- CORS Misconfiguration
23
6
Mitigation Recommendations and Outcome
Hacker Simulations provided a detailed report to the client, outlining the vulnerabilities that were identified and the potential impact of these vulnerabilities.
We worked closely with our client to implement immediate and robust mitigation measures. These measures, crucial for maintaining SOC2 compliance, included patches to address the vulnerabilities, enhanced access controls, and thorough testing to ensure the effectiveness of the fixes.
The client was able to use the report to address the vulnerabilities and improve the overall security of their platform. The discovery and successful remediation of the vulnerabilities underscore the critical role that penetration testing plays in ensuring the security and compliance of their AI Solution. By addressing these vulnerabilities and implementing robust mitigation measures, our client not only protected the integrity of sensitive user data but also took significant strides towards achieving SOC2 compliance.
They continue to work with our company to conduct regular security assessments to ensure ongoing protection against potential threats.

